US megaretailer Target is having a tough time of it.
Having said that, so are its customers – and even, as it now turns out, many of its non-customers, too.
Late in 2013, pretty much half way between Black Friday and Christmas, Target realised it has been, well, the target of an enormous data theft.
As far as Target could tell, its breach wasn’t quite in the very top league, such as those of Adobe and Sony, both of whom had been plundered in the past to the tune of more than 100,000,000 records.
But the breach at Target was epic by any standards, with 40,000,000 payment card records sucked up by cybercriminals.
Early reports suggested that printed CVVs (the three digit codes that only ever appear in printed form on the back of your card) had been stolen along with card numbers, expiry dates and so forth. We were skeptical, as we explained in Episode 127 of the Chet Chat podcast, because the stolen records appeared to relate to in-store purchases, also known as card present transactions, where the CVV is not used. Target subsequently confirmed that these printed security codes were not stolen. That reduces the risk of fraudulent on-line purchases, because card not present transactions usually require the CVV.
Sadly, Target just got promoted to the top league.
The company has now joined the “hundred million plus” data breach club, following its discovery that a further 70,000,000 records were plundered in the raid:
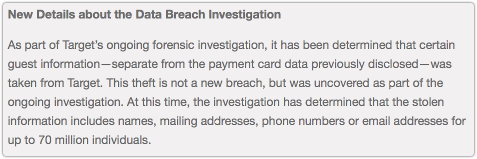
As part of Target’s ongoing forensic investigation, it has been determined that certain guest information – separate from the payment card data previously disclosed – was taken from Target. This theft is not a new breach, but was uncovered as part of the ongoing investigation. At this time, the investigation has determined that the stolen information includes names, mailing addresses, phone numbers or email addresses for up to 70 million individuals.
From this, it seems reasonable to infer that the crooks who got into Target’s network enjoyed much wider rein than was obvious at first, penetrating more than one business system.
Presumably, from Target’s use of the words “guest information,” this additional data wasn’t related only to customers who actually purchased something from one of the company’s stores during the November-December 2013 timeframe, but also potentially to anyone who has ever interacted with Target in any way.
In other words, you may be at risk from this exposure even if you’ve never bought anything from Target.
In some ways, this second part of the breach is worse than the first, because it involves truly personal PII (personally identifiable information).
That’s because, for most people, getting a new credit card is actually much less disruptive, and considerably easier, than getting a new phone number or a new address.
And in case anyone was in any doubt whether a breach is bad for the company that gets breached, Target has the answer.
As well as presenting bad news to its customers and so-called “guests,” the company has had to publish an update to its fourth-quarter financial predictions.
Target is warning shareholders that EPS (earnings per share) will most likely end up at $1.20-$1.30, down from earlier predictions of $1.50-$1.60.
It is also warning of poorer-than-expected sales, despite upbeat performance until the original breach announcement:
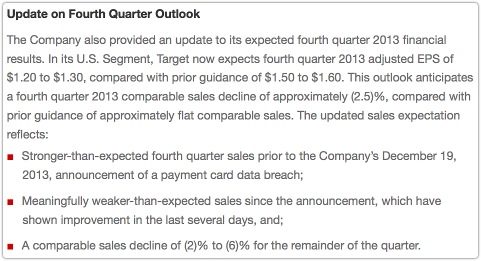
This outlook anticipates a fourth quarter 2013 comparable sales decline of approximately (2.5)%, compared with prior guidance of approximately flat comparable sales. The updated sales expectation reflects:
* Stronger-than-expected fourth quarter sales prior to the Company’s December 19, 2013, announcement of a payment card data breach;
* Meaningfully weaker-than-expected sales since the announcement, which have shown improvement in the last several days, and;
* A comparable sales decline of (2)% to (6)% for the remainder of the quarter.
Target isn’t mincing its words: the breach has hit the company where it hurts.
Let’s hope that there aren’t any more databases that the crooks got into while they were targeting Target.
Via: nakedsecurity




Leave a Reply