New revenue requirements in airline frequent flyer programs are bad news for business travelers.
As many of you know, I do a fair amount of air travel for my day job in the technology industry. One of the few advantages of being a frequent flyer is gaining the coveted “medallion” status on your preferred airline, which includes priority check-in and bag drop off, free checked bags and priority boarding, as well as seat upgrades.
Gaining status on an airline used to be fairly straightforward affair. You accumulated miles, or “points” based on either how many actual miles or how many total “segments” (stops) you flew in a given calendar year, whichever came first, to reach a specific medallion level.
In my case, I was able to make Gold on Delta for CY 2014 due to actual miles flown. The previous year, when I worked at IBM and did mostly regional travel, I reached Gold on total segments.
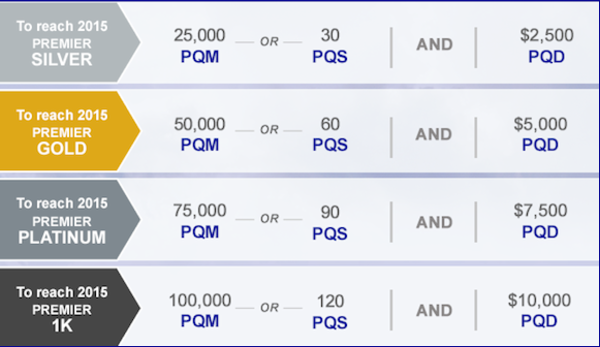
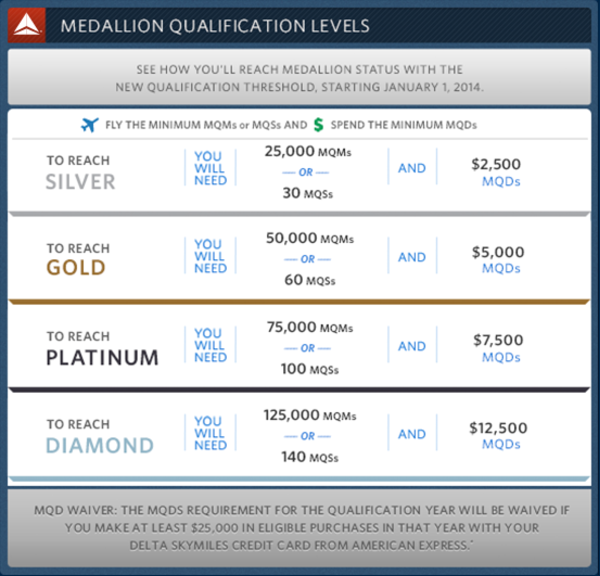
This has now changed for 2014. Two major airlines, Delta and United, are adding another qualifier: Revenue. What this means is that in addition to your miles or segments, you must spend a certain amount of money in tickets to reach that equivalent medallion status. Other large airlines are expected to follow suit.
To maintain my Gold in 2015, I will need to spend $5,000 on tickets in CY 2014.
United Premium Qualifying Dollars for MileagePlus (Click for external link)
There is a certain reasoning behind this that I can sort of appreciate, and it has to deal with the dreaded mileage run. I’ve written about mileage running in years past, and it has become something of a hobby for certain types of flyers who buy dirt cheap tickets on promotion, fly to that destination for one day, and fly back in order to maintain status levels. I think the idea is particularly crazy, but nevertheless, people still did this.
The revenue requirement will certainly cut down on the mileage runners, and it should reduce the amount of people with artificially inflated medallions, in theory. It’s certainly in Delta and United’s interest to downgrade or eliminate medallion members due to the large mergers that both of these airlines have undergone in recent years and vastly increasing their customer bases as a result.
But it also hurts the corporate business traveller who is increasingly being told to control his or her travel costs by booking flights further in advance and also cutting down on travel in general. By buying less expensive tickets, it puts their medallions at risk.
There has been quite a bit of discussion about the new revenue requirements on FlyerTalk, a prominent bulletin board for members of frequent flyer programs.
Delta Medallion Qualification Dollars (Click for external link)
I could live with these new rules if there wasn’t one … um, little additional thing that brings a certain “gaming” element to this system that is now entering the realm of shenanigans that government regulators should as probably be investigating.
As it stands I think “mileage running” is completely acceptable by comparison.
It turns out that on both Delta and United, you can completely waive all of your revenue requirements if you sign up for any of their special credit cards and spend $25,000 per year on them. Delta has a relationship with AMEX, whereas United has a special Chase Visa card for this purpose.
In my case, on Delta, if I qualify for and use their “Reserve” AMEX card, I get an additional 15,000 MQMs for every $30,000 I spend. No pressure, right?
I happen to be a personal American Express Platinum Card customer. I like my Platinum card. It has a unique benefits program, which, for its rather hefty $500-per-year fee, gets me into a variety of airline clubs, and the points that are accrued from spending can be used on a variety of airlines and merchants.
There are a number of tangible benefits with the Platinum that aren’t available on other American Express products, unless you happen to be a Centurion customer, in which case you probably don’t give a damn about medallion statuses anyway. You probably fly on a Gulfstream VI and use gold-leaf-lined toilet paper, and have miniature, lap-sized giraffes as house pets.
Be that as it may, the Platinum is my primary card; I don’t use cash for anything if I can avoid it, so spending $25,000 per year on it between me and my wife is not an issue.
My problem is that I don’t need a $500-per-year Amex Platinum Card as well as a $450-per-year Delta Reserve SkyMiles Amex card. And had this new revenue requirement been in effect for CY 2013, I would not have made my Gold status, because I would have been about $1,000 short on ticket purchases.
So, given my own unique travelling pattern and expected ticket revenue spend, I have no choice but to ditch my personal Platinum and move to Delta’s Reserve AMEX Card (or the Delta SkyMiles Platinum) instead.
This annoys me for a whole number of reasons. First, while Delta’s Reserve Amex card has similar benefits to the AMEX Platinum card, they aren’t exactly the same. Second, the points accumulated on this card are not as flexible with merchants as the Platinum.
I can get into Delta’s SkyClubs and those of their SkyTeam partners, but not other airline clubs such as American’s. I also can’t use the points other than Delta or a SkyTeam partner if I want to book tickets for personal travel, say, for vacation use.
And if I want to convert my Platinum card awards points to Delta points? There are transfer fees involved. It actually makes more sense to downgrade my Platinum to a Green card, and maintain it just to keep my rewards points as flexible as possible until they are all spent.
All in all, I think this new revenue requirement and Credit Card shenanigans by Delta and United are awful for their most valued customers.
Via: zdnet