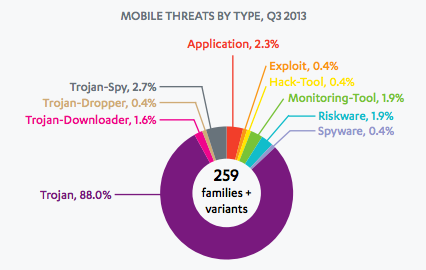
IT spending is kicking up again, but training budgets have been slow to recover.
Linda Bubbers got a tip early in her career: Become a Certified Netware Administrator and earn a transfer to a better team.
Bubbers, a Cobol programmer at the time, took the advice. She paid for the CNA course and test herself, banking that the certification would indeed help her get ahead.
It did. And so for the past 20 years Bubbers has followed the same strategy for career success, earning multiple certifications through studies she funds out of her own pocket. She estimates that her ongoing education, which includes structured classes, conferences and books, has cost her at least $14,000. She spent another $9,000 earning an MBA from Webster University.
“I just kept doing it on my own because I wanted to advance, but also this is what IT people need to do to stay employed. Everything changes so fast, you can’t not stay in the education stream,” says Bubbers, now a senior network administrator at Craig Technologies, an IT and engineering services provider in Cape Canaveral, Fla.
Bubbers is hardly alone in her approach. IT spending may be on the rise, but training budgets aren’t increasing at the same pace. That has left many IT professionals shouldering more of their own training costs as they seek to keep up with the rapidly changing technology landscape.
In fact, in a Computerworld survey of 489 IT professionals conducted in August and September, 62% of the respondents reported that they have paid for training out of their own pockets in order to secure their careers. They listed “keeping skills up to date/being valuable to employer” and “finding an appropriate new position for my skill set” as their two biggest career concerns. And 78% said education has been either very important or important for their careers.
They’re on the right track, says Jack Cullen, president of Modis, a global provider of IT staffing services.
“IT workers are right when they say this is an expectation, because given what IT jobs pay, the expectations from employers are high,” Cullen says.
He adds: “It’s a very competitive field, and this is what you have to do to stay competitive.”
That’s not to suggest that an IT professional has to get every certification under the sun to stay employed or land a big promotion. But, he says, the plum jobs and assignments do indeed go to those who have the extra education on their resumes.
Training as Table Stakes
IT is hardly the only field with such high expectations for ongoing training. As Cullen points out, people in many other lines of work face similar pressure to continually seek professional development opportunities. In fact, some professionals, such as CPAs, lawyers and medical personnel, are required to take a set number of hours of training if they want to retain their licenses or rights to practice.
“If you really think about it, IT is playing catch-up to what other professions have been doing for years,” Cullen says.
Some IT workers approach training the same way people in other professions do — with the sense that it’s essential to their careers.
Take Chante Nelson, an information systems analyst for Florida’s Broward County. She started in IT soon after joining the U.S. Navy in 2000 and remained in the field after receiving an honorable discharge in 2008.
She earned a bachelor’s degree in systems security from the University of Phoenix in 2011 and a master’s degree in information systems, also from the University of Phoenix, in August. She paid the nearly $50,000 tuition bill using her own money, loans and grants.
In addition, Nelson has paid for a number of seminars and training courses covering everything from Microsoft products to VMware. And she covered the costs for programs that helped her earn A+, Security+ and Network+ certifications as well as the Microsoft Certified Solutions Expert designation. She figures she spends eight to 20 hours a month in some sort of training program.
Nelson picks courses based on what she knows her employer will need as well as what’s hot in the field.
“You weed it down a little bit to what the company needs and then you ask if it’s going to be beneficial for me for the future. You don’t just want to do it for the company and have skills that won’t be useful anywhere else,” she says.
That approach has helped her get ahead. Nelson has held three jobs at three different organizations since 2008, with each position a step up from the prior one.
However, she questions whether such efforts will continue to stand out on her resume. She says employers seem to expect IT staffers to pursue ongoing education just to stay employed.
“I think it’s becoming more so that you have to have it, it’s not even putting you over the edge to know all these things,” she says. She points to a colleague who was told by a potential boss that even though a job posting listed a number of certifications as “preferred,” he really required them.
The courses that are most in demand seem to correspond with the most sought-after skill sets, with the popular training topics depending on the individual’s specialty, according to both IT workers and those who hire them. Networking pros gravitate toward Cisco certifications. Project managers seek out courses that can help them earn the Project Management Professional designation. Developers are trying to sharpen their mobile app development skills. Those looking to move into management are taking business courses and enrolling in MBA programs.
“You can almost break it down by position,” says Joseph Kotlinski, a partner and manager in IT search at WinterWyman, a Waltham, Mass.-based recruitment firm.
Kotlinski says system administrators are signing up for training sessions in Linux and Windows administration and in Perl, PHP, Python and Ruby on Rails. People who know .Net and Java want to learn about mobile and open-source technologies. Database folks want to learn more about SQL, MySQL, Hadoop, Cassandra, and big data in general. And everyone wants to learn about cloud computing.
Kotlinski agrees that IT professionals need to keep up with their training if they want to keep their jobs.
“The business expects the technical people to really know what’s going on out there,” he says. “There are a lot of people in companies who are gadget people, and you don’t want those people to know more than the technology people, so the IT people [train] just to stay current, but also so they can provide services and guidance to those gadget people.”
Many pay for training so they can check off the certifications and skills that job postings list as requirements, just to make it past the screening process.
On the other hand, Kotlinski says, some techies sign up for extra training simply because they’re curious.
“They want to know what’s out there. If they hear someone mention a new technology, they want to know what it is,” he says.
Training Potpourri
Kotlinski and others say they’re also seeing new trends in how and where IT workers seek training. Although many corporate development budgets remain tight, companies still pay for some training. They might not be sending large numbers of staffers to big conferences and seminars, Kotlinski says, but they continue to contract with vendors for on-the-job training or encourage mentoring and other work-based learning.
IT workers may not see all of those learning opportunities as training. And they might not realize that their companies are still willing to pay for training. IT leaders say many employers cover training costs, even for courses picked by individual workers, as long as a worker can show how the training benefits the company. Still, they acknowledge, training dollars aren’t flowing as freely as they once were, and that leaves plenty of costs to individual employees.
And that scenario has serious drawbacks, says Joseph Young, IT director at OK International, a Garden Grove, Calif.-based manufacturer of bench tools, equipment and related products.
Young says he pays for the training he thinks his six-member IT team needs so that he — and therefore his organization — can stay current. “I just make sure they can quantify how their training will help the company reach strategic goals,” he says, noting that he supports a variety of training opportunities, from conferences to mentoring.
He says IT organizations that don’t pay for training lose their competitive edge. “There’s a common denominator I find with underperforming IT organizations: They don’t have the investment in training,” he says.
As a result, many techies must find ways to keep costs in check as they pay for more and more of their ongoing education. They seek out webinars and low-cost or free online learning opportunities, including massive open online courses, or MOOCs.
Ali O. Sabbah is a case in point. He’s a senior desktop analyst at a California law firm. He’s studying for a bachelor’s degree in business law and finance at California State University, and he takes courses in networking, Cisco certification and emerging technologies. He signs up for vendor-led training at his company, classes at an area community college and tutorials online.
He acknowledges that it’s an eclectic mix, but he says it’s delivering the knowledge he needs to earn his degree and the certifications he believes he’ll need to eventually launch his own IT services firm. “There’s enough out there,” he says, “that I can get what I need to get ahead.”
Via: itworld