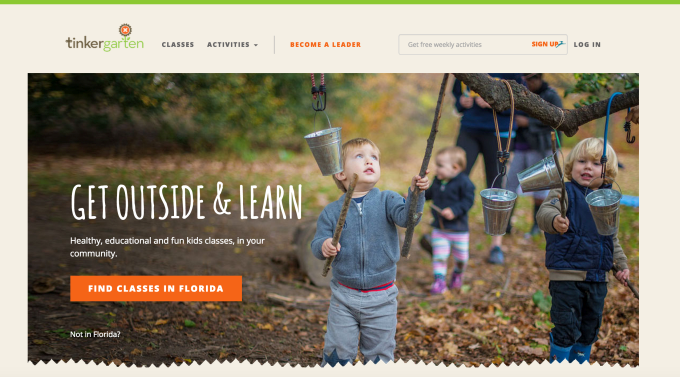
Many parents today recall childhoods where we were pushed out of the house by our parents, while told simply to “go outside and play.” But our children seem to be growing up in a different world: one filled with scheduled activities, hovering parents, and a lot of screen time. A new startup called Tinkergarten, now backed by half a million in seed funding, wants to change that by offering a technology platform that enables a distributed workforce to host play-based learning classes for kids that take place outdoors in parks and other green spaces.
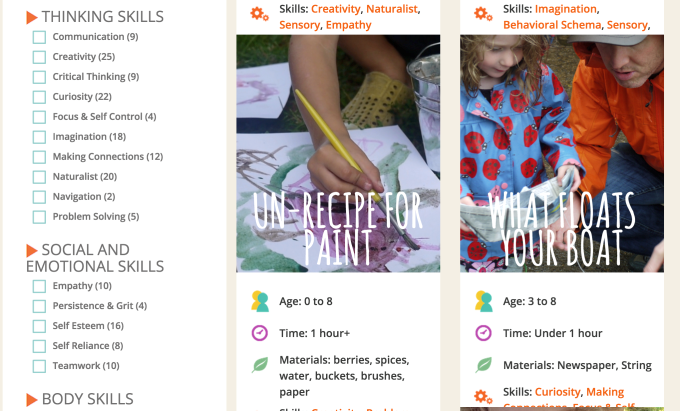
The idea is to encourage kids to have fun and be social, while developing various skills through hands-on activities that range from making mud pies to creating art using items found outdoors, like leaves and berries. But instead of structuring the class in a way where kids are told what to do, they’re encouraged to problem-solve in order to foster their independence.
For example, a teacher might say that today they want to make mud pies, but she forgot to bring the mud. The kids then brainstorm how they can create the mud using the dirt and water at the park. (Yes, the classes can get messy!).

If that problem sounds too easy, it’s because the program is aimed at a younger set of students – Tinkergarten classes are focused largely on attracting the “Mommy & Me” crowd with activities for children as young as 18 months old and up. The curriculum is being developed to support kids up to 8 years old, however, but a lot of the interest comes from parents looking for an alternative to constant playdates as a means of socializing their toddlers.
The idea for Tinkergarten comes from co-founders and husband-and-wife team Brian and Meghan Fitzgerald. Brian has a lengthy background in the tech industry, working for both startups and larger companies, including Yahoo, Audible, Amazon, and Knewton, and Meghan is a former teacher and elementary school principal.
As parents of three girls, the Fitzgeralds initially began Tinkergarten as a side project, hosting classes themselves, but later realized there was a potential business involving setting up a platform that would allow others to receive training and host their own classes anywhere in the U.S.
While, like many, the two have an appreciation for today’s technology-fueled world, they were also concerned that children weren’t given enough time to just “play” out in the real world.
“We were worried that they’re not going to be able to invent things without technology, or to be outside specifically,” explains Meghan. “Will they be able to think freely? Does time outside really matter to people? And what is this lack of time outside doing to kids?”
With Tinkergarten, prospective teachers are vetted through background checks and other processes similar to other on-demand startups, then offered virtual training through an online portal. They then purchase the initial materials needed for classes, like buckets, tarps, rope, tweezers and more, but subsequent materials are provided by the company.
Through the site, teachers can configure their schedules, customize their curriculum, communicate with parents by messages sent out via email and SMS, manage photo-sharing, and more. The idea is to provide a single place for the teachers to run their own programs, allowing them to earn extra income. With classes that range from $25-$30 per session, and are hosted a couple of times per week for different age groups, teachers have the potential to make a few thousand extra dollars, or as much as $10,000 extra per year.
Currently, the company has 30 class leaders signed up in the New York Metro area, including Manhattan, Brooklyn, Westchester, Northern N.J. and Southern Connecticut, and is now preparing to expand its platform nationwide. Tinkergarten generates revenue by splitting the class fees (they keep 70 percent) with teachers. The founders explain that split is necessary because of their investment in the technology infrastructure, the ongoing support, and the materials provided.
For parents, the classes could offer a nice alternative or addition to a kid’s schedule, which tends to favor more structured fare like dance, music and sports – even at young ages. But the classes are priced in the premium tier. At $100 per month and up for a once per week class, parents may have a hard time wrapping their heads around the value associated with outdoor time and mud pies when, for the same amount, they could put their kid in (possibly two!) more traditional classes.
That could limit Tinkergarten’s potential for growth and could see it needing to find a different way to monetize – like white labeling its tech platform for the extracurricular activity industry in general, perhaps.
The startup is today a team of five full-time based in Brooklyn and Northampton, Mass. Investors in the company include Brooklyn Bridge Ventures, Structure Capital, and edtech entrepreneurs John Katzman (founder of 2U, The Princeton Review, Noodle), and Don Katz (founder of Audible).
Via: techcrunch