Stealing payment card data has become an everyday crime that yields quick monetary gains. Attackers aim to steal the data stored in the magnetic stripe of payment cards, optionally clone the cards, and run charges on the accounts associated with them. The topic of PoS RAM scraper malware always prompts businesses and retailers to ask two important questions: “How do I protect myself?” and “What new technologies are vendors introducing to protect businesses and consumers?”
This blog entry seeks to answer these questions by discussing a PoS Defense Model and new technologies that can protect businesses and consumers from PoS RAM attacks.
PoS Defense Model
Based on our analysis of the PoS RAM scraper attack chain and PCI-DSS and PA-DSS requirements, we have created a multi-tiered PoS Defense Model that businesses and retailers can implement to defend against PoS RAM scraper malware attacks.
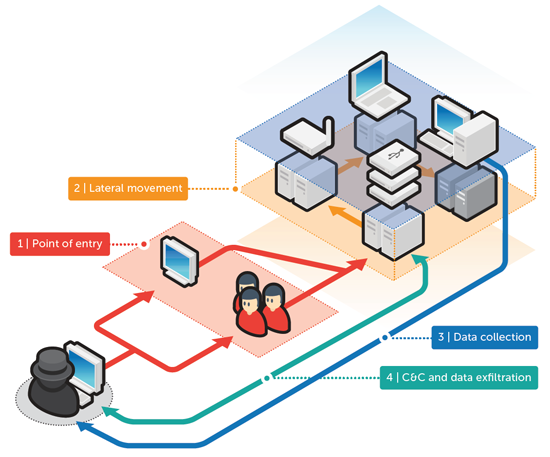
Figure 1. Multi-tiered PoS Defense Model
The four layers of the PoS Defense Model are:
-
Infection Layer – this is the first and most important line of defense against PoS RAM scrapers as it aims to prevent initial infection, or block the malware’s execution before it causes damage.
-
Lateral Movement Layer – if the infection layer fails to stop the malware, then the next layer of defense aims to identify suspicious or malicious behavior when the malware attempts to spread and blocks it.
-
Data Collection Layer – PoS RAM scraper attacks might involve other information stealing components that sniff network traffic and keylogs, and steal sensitive files. This layer of defense aims to prevent data theft.
-
C&C and Data Exfiltration Layer – the stolen credit card data is only valuable after it has been exfiltrated from the victim machine. The final layer of defense aims to prevent the malware from communicating with the C&C servers and prevent exfiltration of stolen data.
We have identified 26 defensive technologies and strategies that businesses and retailers can implement in their environments to defend against PoS RAM scraper attacks. The following Venn diagram shows these defensive technologies and strategies placed within the PoS Defense Model.
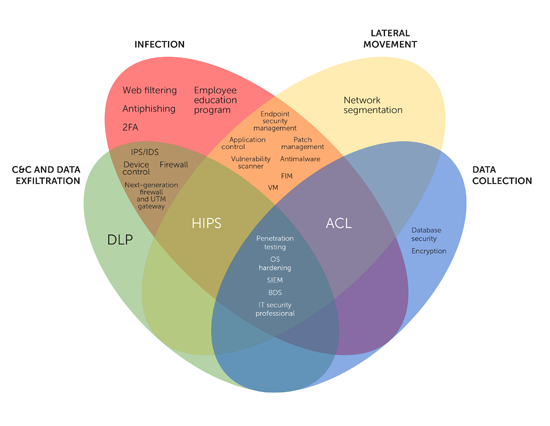
Figure 2. Defensive technologies and strategies (click on the image to embiggen)
Next Generation Payment Technologies
The new reality is that any Internet-connected device that processes payment card data should be viewed as a data theft target. Buyer security rests on the shoulders of several key players – device manufacturers, service providers, businesses, banks, and even credit card brands. Strong IT defense goes a long way in preventing PoS system breaches but it is not a magic bullet. New secure payment technologies must also be deployed alongside strong IT defenses to protect against PoS RAM scrapers. Two technologies that are being widely deployed are:
EMV or Chip-and-PIN cards

Figure 3. Encrypted data stored in chip (outlined in red)
EuroPay, MasterCard, and Visa (EMV) is the global standard for Integrated Circuit Cards (ICC). EMV cards store encrypted Tracks 1 and 2 data on a chip in the card. This chip stores a cryptogram that allows banks to determine if cards or transactions have been modified. It also stores a counter that gets incremented with each transaction. Duplicate or skipped counter values indicate potential fraudulent activities. The EMV cards interact with PoS terminals that have ICC readers and use the EMV-defined protocol for transactions. Similar to debit cards, cardholders need to input a PIN for authentication before the transaction is processed.
Encryption plus Tokenization
PoS RAM scrapers will have nothing to steal if credit card Tracks 1 and 2 data are not present in the PoS system’s RAM. This is the underlying principle behind the new payment processing architectures being developed and deployed today. One implementation uses tokenization, a process that replaces a high-value credential such as a credit card with a surrogate value that is used in transactions in place of the high-value credential, and encryption.
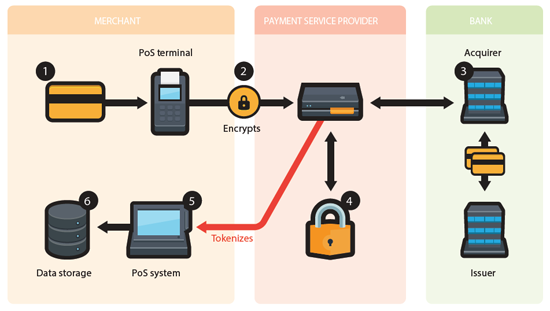
Figure 4. Process flow for Encryption and Tokenization
The workflow is as follows:
-
Customer swipes their credit card at the merchant’s PoS terminal to complete the purchase.
-
The PoS terminal reads and encrypts the credit card data and transmits it to the Payment Service Provider (PSP) for processing.
-
The PSP forwards the credit card data to the banks (acquirers & issuers) for authorization.
-
The PSP uses a tokenization algorithm to replace the actual credit card data with a token.
-
The generated token and bank authorization status is send back to the merchant’s PoS system.
-
The merchant’s PoS system stores the token instead of the actual credit card data in all places.
The Future for PoS RAM Scraper Attacks
As PoS RAM scrapers become more prominent threats, big businesses will heavily invest in cybersecurity to prevent attacks against their PoS environments. Attackers will thus refocus on SMBs, as these may not necessarily have the cybersecurity budgets that enterprises have to prevent PoS system breaches. We expect to see more SMBs get compromised, which will collectively be a bigger breach than compromising a few enterprises.
Rollout of new security measures will significantly change the PoS playing field for attackers. As businesses upgrade to new secure payment systems, attackers will attempt to come up with new strategies against improved systems and environments.
For an in-depth analysis about protecting your business against the threat of PoS RAM Scraper malware, please read the Trend Micro paper, Defending Against PoS RAM Scrapers – Current and Next-Generation Technologies.
Via: trendmicro




Leave a Reply