Here’s a quick note about an important issue!
Mozilla has patched a bug in its cryptographic library, NSS.
NSS stands for Network Security Services, used by Mozilla products such as Firefox (web browsing), Thunderbird (email) and SeaMonkey (both).
All these products have now been patched, including the Firefox Extended Support Release (ESR) versions.
→ As far as I am aware, Google’s Chrome and Chromium browsers, as well as Opera, also use NSS.
The bug is rated “critical” because is deals with the validation of digital signatures in TLS connections.
TLS (Transport Layer Security), often also known by its old name of SSL (Secure Sockets Layer), is the cryptographic protocol that puts the S in HTTPS.
When you use HTTPS, it’s not just confidentiality you are after, but also integrity (to stop a crook fiddling with the message in transit) and authenticity (to stop a crook claiming to be your bank).
Without certificate validation, you could easily end up conducting a totally secure and unsniffable interaction…
…with a complete imposter.
Unfortunately, this recently-patched NSS vulnerability affects digital signature verification in all the above mentioned products.
Phishing HTTPS logins
Remember that crooks who have hacked into your Wi-Fi access point – at your local coffee shop, for instance – could sneakily redirect any of your HTTPS logins to phishing sites instead.
Usually, however, the crooks can’t present a digital certificate to vouch for the fake site they have drawn you into.
Sometimes, the crooks avoid the need for digital certificates altogether by dropping back to a plain old HTTP site that doesn’t use encryption at all.
You should be able to spot this sort of ruse due to the absence of any security indicators in the address bar of your browser.
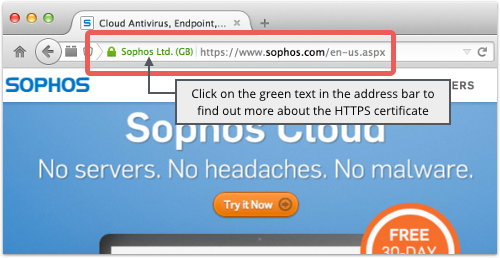
Or the crooks could present a TLS certificate that claims to be from your bank, but which isn’t vouched for by any recognised certificate authority.
You should be able to spot this sort of ruse due to an “untrusted connection” warning from your browser.
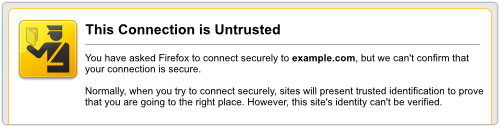
But if there’s a cryptographic vulnerability that can be exploited to make a bogus digital certificate seem valid, then the crooks may be able to redirect you to an imposter site without raising any alarms.
And that could lead to the digital theft of your personal information, including usernames and passwords.
Get the latest update
If you have a software product (e.g. Firefox) that uses NSS, make sure you’ve got the latest update; for Mozilla software, that means (at 2014-09-24T23:45Z):
- Firefox 32.0.3
- Firefox ESR 24.8.1
- Firefox ESR 31.1.1
- Thunderbird 31.1.2
- Thunderbird 24.8.1
- SeaMonkey 2.29.1
For what it’s worth, I’m using Firefox 32 on OS X, and the update was so small I didn’t get time to read its size during the download.
Applying the update was quick: less than a second to download the patch, and a few more seconds to restart the browser process.
So my recommendation is, “Just do it.”

Worried about rogue Wi-Fi access points?
Why not run a secure VPN from home?
Download our full-featured Sophos UTM Home Edition for free…
Via: sophos




Leave a Reply