T9000 is being used in targeted attacks against U.S. organizations.
Researchers found a complex backdoor malware which targets Skype, capturing video, audio, and chat messages as well as grabbing screenshots and stealing files, before sending the data back to the attacker.
Researchers at Palto Alto Networks analyzed a new variant of backdoor malware that goes to “great lengths to avoid being detected and to evade the scrutiny of the malware analysis community.” T9000 is a newer variant of T5000, or the Plat1 malware family that APT actors used in spear phishing attacks after the disappearance of Malaysian Flight MH370. T9000 is being used in targeted attacks against multiple U.S. organizations, dropped by a RTF file, but its functionality indicates the malware is “intended for use against a broad range of users.”
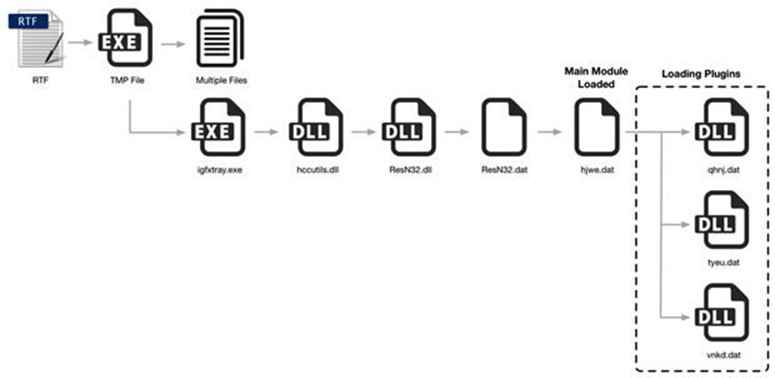
Instead of having limited functionality, T9000 is described as complex, as it uses a multi-stage installation process to evade detection and fly under the radar. In stage one, researchers explained that T9000 “goes to great lengths to identify a total of 24 potential security products that may be running on a system and customizes its installation mechanism to specifically evade those that are installed.” Those security products include: Sophos, INCAInternet, DoctorWeb, Baidu, Comodo, TrustPortAntivirus, GData, AVG, BitDefender, VirusChaser, McAfee, Panda, Trend Micro, Kingsoft, Norton, Micropoint, Filseclab, AhnLab, JiangMin, Tencent, Avira, Kaspersky, Rising and 360.
When a malicious DLL is loaded in stage two, T9000 again queries the security products and then – depending upon what it found – uses one of three separate techniques for starting stage three. The core malware isn’t loaded until stage four, but it checks for running processes and will exit without performing malicious activity if those processes are found. The victim’s username and OS version are sent back to the attacker via C&C server, which then sends specific modules to steal data.
The first plugin runs multiple threads, taking screenshots of the desktop, monitoring the foreground window every 20 seconds, and collecting information from Skype. If Skype is running and the victim is logged in, then the target will see a dialog box asking to allow explorer.exe to access Skype.
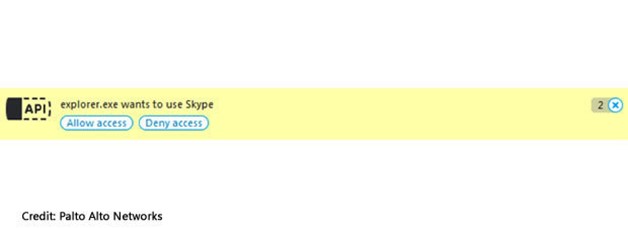
Just say no, as the researchers pointed out:
The victim must explicitly allow the malware to access Skype for this particular functionality to work. However, since a legitimate process is requesting access, the user may find him- or herself allowing this access without realizing what is actually happening. Once enabled, the malware will record video calls, audio calls, and chat messages.
T9000 steals documents and more – even from removable drives
If a victim did allow access, then T9000 also sets out to steal other files, such as documents, presentations, and spreadsheets – even those on a removable drive – including the file types: .doc, .ppt, .xls, .docx, .pptx, .xlsx. The FlaskDiskThief plugin allows the attacker to “collect files that are being passed around from one machine to another via removable drives.”
The third plugin logs any changes, such as when a file is created, copied, moved, or deleted. The researchers suggested attackers use it “to record important actions taken by the victim, which in turn may allow them to gain additional access as well as insight into the victim’s actions.”
Palto Alto Networks included a list of indicators of compromise; the researchers hope that by sharing the details of how T9000 works, then it will help others defend themselves against the backdoor malware’s attacks.
Via: networkworld




Leave a Reply